
ENAR
Technologies
Technologies
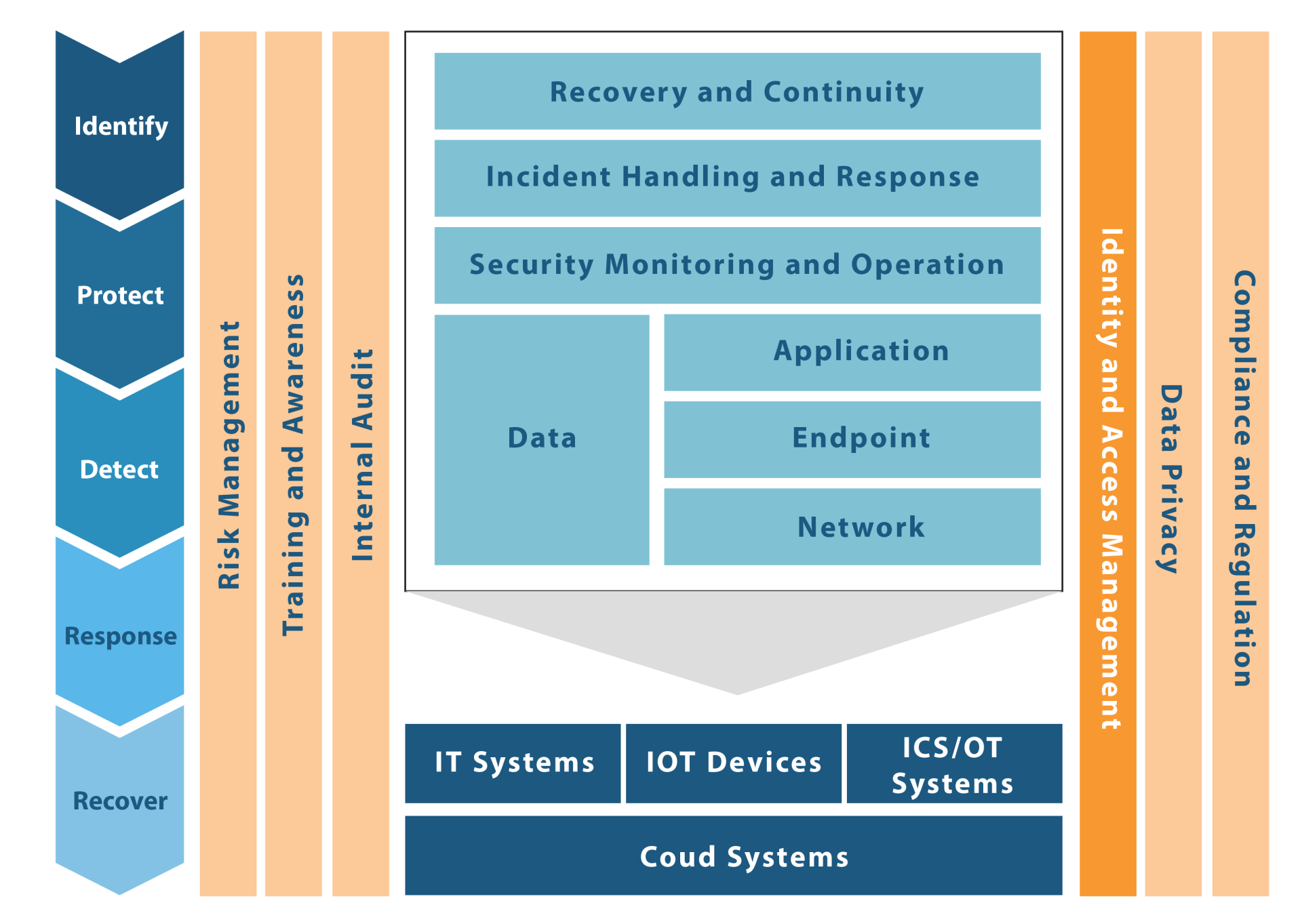
Asset Management
Since the protection methodologies have to be determined in accordance with the characteristics of the asset to be protected, it is an important requirement that the institutions and organizations know the inventory of the assets they would like to protect and that this can be kept up to date with the dynamic digital world. It is one of the first steps of security to follow the network structure and follow the inventory of hardware and software included in this network. The solution that we represent in this area is ASMA.
Authorized Access and Password Management
Authorized users are those who have direct access to the most valuable data and systems of an institution or organization. These access privileges are also of direct interest to an attacker and may be used to circumvent such users. they are the target of many attacks. The solution of this problem is to transfer the management of authorized accounts to a system and to enable the users to carry out their operations by using the unauthorized, standard users by taking authority over this system. Thanks to this structure, it is ensured that both the authorized user passwords can be managed and the connections made can be recorded.
Bandwidth Optimization
It is important that the wide area network and many services running on it provide regular service with minimum delay. Prioritization of some of the traffic or applications that are important within the organization increases the performance of the application and data communication by significantly reducing the bandwidth usage. In this way, the number of applications that can work instant and the number of connections is also increased. There is a flexible usage area including disaster recovery centers, remote offices, data centers, cloud and virtual infrastructures.
Border Security Analysis System
One of the most important handicaps of security systems, which are positioned for protection purposes, is that they depend on people who manage these systems and they cannot provide the security that they promise in configuration errors. Testing of the performance of these systems on a regular basis and revealing the weak points of defense are considered as an important safety issue.
Cyber Threat Intelligence
In order to prevent an attack, it can be detected and countermeasures should be taken. Cyber Threat Intelligence also emerges at this point to provide the current intelligence data for institutions and organizations with various mediums and tools and to prevent these attacks from being initiated at the early stages.
Data Leakage Prevention
Institutions and organizations must protect their data against any leakage of data that may arise from internal or external threats. Data leak/loss USB sticks can be made in many ways, such as taking screenshots, moving data over the network, transferring to other sites via encrypted paths, and sending them via e-mail. It is important to use a data loss/leak prevention (DLP) solution on end-user systems and network entry/exit points so that data that does not want to exit does not come out. Legislation and institutional standards (PDPL, GDPR, etc.) trigger this need.
Database and File Server Firewall
In many IT infrastructures, information is usually found on database servers and file servers. Institutions and organizations must protect their data against any leakage of data that may arise from internal or external threats. In particular, legislation and institutional standards (such as PDPL, GDPR ...) trigger this need.
Database servers are one of the most critical assets to be protected
Database servers are one of the most critical assets to be protected
DNS Security
Name inquiry is the backbone of the internet structure. Ensuring corporate identity and accessibility is only possible with DNS structures. Although this structure is so important, its security has remained second and has been the basis of many attacks. With DNS Security solutions, it can work as high-performance DNS servers and can provide security against attacks.
DoS/DDoS Protection in Cloud or On-Site
DDoS attacks are a kind of attack which is especially prominent with the spread of IoT systems and the emergence of new types of pests. As a result of DDoS attacks, bandwidth is consumed, Internet infrastructures are affected, communication is delayed and service is stopped, and as a result, loss of prestige leads to loss.
DDoS protection can be provided on-premise, on cloud and in hybrid for
DDoS protection can be provided on-premise, on cloud and in hybrid for
E-Mail Security
Because of an e-mail system is one of the most common written ways of communication, it is a way frequently used by informatics hackers. Many malicious files and untrue information can be sent by e-mail and they can direct the victims to command control centers for data leakage. Inbound and outbound traffic of the e-mail servers must be checked in depth and no harmful files or messages should be transmitted to the user after a series of checks. E-mail security systems can be positioned as an external server that can control the SMTP traffic of e-mail servers. In addition, e-mail can be installed on the server and internal traffic can be scanned for unwanted pests. Some capabilities of e-mail systems are as follows;
- Advanced Antivirus Protection
- Antispam, Content Filtering
- Zero Day Attacks (APT) Protection
- Reputation control
- Quarantine Management
- SIEM/Syslog Integration
- Reporting Management
End User Security
In recent years, millions of users and systems have been damaged by millions of new malware variations, ransomware and zero-day threats. Organizations have been severely affected by this situation and many manufacturers are developing solutions to prevent these threats through different methods. Instead of traditional end-user solutions, the following solutions provide more effective protection;
- Advanced malicious code analysis
- Heuristic analysis
- Integration with APT (zero-day attacks)
- Network attack prevention and firewall module
- Application control
- Device control
- IOC detection and blocking
- Integration with data leakage prevention (DLP) system
Firewall/Network Configuration and Change Control
IT infrastructures can include firewall, attack prevention systems and network products from many different manufacturers. Configurations on these components need to be checked for compliance with certain regulatory and institutional standards. Some features can be used at this point;
With the help of Firewall Control, you can perform many independent checks, normalization, hidden risk factors, weakness analysis on all firewalls within your infrastructure within the framework of specific legislation, corporate standards and special criteria you can determine and you can get customized reports for them.
With the help of Network Configuration Control, it provides network visibility from medium-sized infrastructures to large-scale infrastructures. You can create a network topology model, including end-to-end physical, virtual, and cloud infrastructure, and control compliance with legislation and enterprise standards using all network components on the resulting model. You can also test targeted configuration test scenarios and communication problems on the generated network model.
With the help of Change Control, you can put all the changes on the firewall components in the infrastructure into a workflow and follow up the process by the security units. In this way, every rule change can be converted into a demand and checked whether it is implemented in a way appropriate to the workflow.
With the help of Firewall Control, you can perform many independent checks, normalization, hidden risk factors, weakness analysis on all firewalls within your infrastructure within the framework of specific legislation, corporate standards and special criteria you can determine and you can get customized reports for them.
With the help of Network Configuration Control, it provides network visibility from medium-sized infrastructures to large-scale infrastructures. You can create a network topology model, including end-to-end physical, virtual, and cloud infrastructure, and control compliance with legislation and enterprise standards using all network components on the resulting model. You can also test targeted configuration test scenarios and communication problems on the generated network model.
With the help of Change Control, you can put all the changes on the firewall components in the infrastructure into a workflow and follow up the process by the security units. In this way, every rule change can be converted into a demand and checked whether it is implemented in a way appropriate to the workflow.
ICS Asset Management
Although Industrial Control Systems (SCADA) are mostly seen as static structures, investigations and researches reveal that even the inventories of these structures are not known or are not up to date. Monitoring the changes in the environment where these mission critical systems work and keeping this inventory dynamically are as important as the IT structures.
ICS Firewall
Industrial Control Systems (ISC/SCADA) production facilities are seen as the most important job title for energy and infrastructure providers. Although it is assumed that they are in closed networks, new needs and accessibility requests have started to open these systems to wide area network. The differences in the protocols used are very different from the IT structures in the areas where these components are located. The most important priority is the use of rugged systems that can work in environments where it can be exposed to bad conditions. At the same time, a system that can understand the communication protocols used will detect anomalies and a solution must be used to prevent the building from being prepared.
ICS Vulnerability Management
Industrial Control Systems (SCADA) are composed of components with certain basic functions. Although these systems seem simple, the systems and software operating within them do not differ from the IT systems in general. These softwares also contain various vulnerabilities such as the like, and are evaluated by the authorities that their exploitation can have critical effects. In order to establish an effective security structure, it is necessary to determine the weaknesses of these systems and to take necessary precautions but due to the sensitivity of the structure, active scanning methods cannot be used. It is possible to protect the OT (Operational Technology) structures with an effective weakness management by using passive vulnerability detection methods.
Information Security Management System
Information Security is evaluated under the titles of Human, Process and Technology. Even if the process part is present as an abstract concept, Information Security Management Systems are used in order to ensure that the structure can be tracked correctly, the processes formed are conformed to the system they are referenced and can be delivered to the needy in an effective manner.
Intrusion Detection and Prevention System
Traditional detection methods can overlook advanced attacks. A single mechanism that can detect malicious software is not enough to prevent all attacks. Besides signature-based operating system, it is effective in preventing malicious software which is not expected to be found in unsigned detection engines. In addition, threat intelligence, application control, APT (zero-day attack prevention) system, SIEM and many more features/integration are available. The intrusion detection and prevention system (IPS) system can be configured topologically on virtualization platforms or at network level (inline or sniff).
Load Balancing and Application Acceleration Technologies
Load Balancing and Application Acceleration Technologies, which are used due to increasing business needs and better service requirements, can enable many different services and vehicles to operate in a performance manner.
Modern Malware Code Analysis and Blocking System
The vast majority of today's threats are known as zero-day attacks, and that harmful, persistent and transformed files reach the network. Because these types of threats cannot be detected by conventional methods, however, the real threat can be detected with systems that can monitor their behavior and monitor the movement of the file in a sandbox. The Checkpoint SandBlast APT solution is one of the industry's leading and most successful solutions at this point. ATP systems are integrated with some existing security components (firewall, proxy, smtp gw) and can send the files passed over HTTP, HTTPS, SMTP and SMB / CIFS protocols to the APT system. With this method, creating a point of error on the network can be prevented, as well as the first access to the network by analyzing the file can be prevented from reaching inside and literally zero-day protection can be provided.
Network Access Control
Nowadays, corporate networks serve many traditional and non-traditional systems, as well as tablets, smartphones, industrial control systems, virtualization platforms, wireless access points and cloud-based applications. The infrastructures with such diversity facilitate the work of IT hackers. Network access control systems (NACs) must manage these assets and control unauthorized access.
There are two types of NAC solutions. These approaches, which can be summarized as asset or user based NAC, have the advantages that are shaped according to needs. A security-centered NAC solution contributes greatly to both asset management and classification, as well as to detection and automated response processes. Integration of NAC solutions with the following security components can also be provided;
There are two types of NAC solutions. These approaches, which can be summarized as asset or user based NAC, have the advantages that are shaped according to needs. A security-centered NAC solution contributes greatly to both asset management and classification, as well as to detection and automated response processes. Integration of NAC solutions with the following security components can also be provided;
- Advanced Threat Detection (ATD)
- Enterprise Mobility Management (EMM)
- Endpoint Protection Platform/Endpoint Detection & Response (EPP/EDR)
- IT Service Management (ITSM)
- Next-Generation Firewall (NGFW)
- Privileged Access Management (PAM)
- Security Information & Event Management (SIEM)
- Vulnerability Assessment (VA)
- Open Integration Module (OIM)
Network and Application-Based Data Encryption
In order to prevent data from being transmitted in an undesirable area, data encryption must be performed according to data criticality. The cryptographic force should be calculated according to the time when the data will be lost. Security and confidentiality can be ensured in this area by ensuring that the data is encrypted when passing through untrusted network structures or in application database.
Network and Endpoint Forensic Analysis Software
A significant number of incident response processes are related to collecting and analyzing evidence-related data. This data is also associated with the event, endpoints, servers, and are on the network. With Forensic Analysis solutions, it is possible to collect these data live and to store them for later review.
Network Performance Monitoring
Problems with network infrastructures must be identified before impacting the workflow. It is important to understand whether a problem in the application is caused by network components. Using network performance monitoring system, packet feeds from popular flow sources such as Netflow, sFlow, J-Flow, IPFIX can be monitored, reported and analyzed. In addition, packet analysis can be performed in real time at the time of the problem using the packet capture feature.
New Generation Firewall
New generation firewalls can operate in virtual, cloud and physical infrastructures with centralized management, flexible expansion capabilities, high and different network interface supports.
The next generation firewall has some of the following basic functions;
The next generation firewall has some of the following basic functions;
- Application Control
- Attack Prevention System
- Anti-Virus Protection
- Zero-Day (APT) Protection on-premise or Cloud
- URL/Web Filtering System
- Active Directory/LDAP Based Rule
- Anti-Bot Protection
- Anti-Spam Protection
- Bandwidth Check
Packet Routing System
The increase in the number of security systems and the complexity it brings to the network structure increase the operational costs considerably. Packet Routing systems provide a central and high performance environment for data to be collected in network (L2) or mirror (span, tap) method, and provides an effective method for placing these systems in desired network network. Thanks to this system, the connection complexity is reduced, the load in the switch structure is reduced and the ability to be optimized in the traffic routed to the security systems emerges.
Security and Networking Products Center Backup
Backup and return scenarios are necessary to reactivate the infrastructure as a result of an attack and / or a disaster as soon as possible. As a result of this approach, we can say that backup systems are a part of security. The simple and fast return of backup systems will shorten the time the systems can resume operation in the event of a disaster. It is the basic expectations that the support system of the backup system is rich, that the received backups are kept safely and that the backups are taken.
Security Incident Management and Automation
Detection of security incidents raises the next step, the Event Response processes. It is very difficult in this respect to ensure that the large amounts of events identified are removed by manpower and that the incident intervention process focuses on important events. At each Cyber Security Operation Center, which has reached a certain level, this human resource gap is emerging and a mechanism is created that will enable the manpower to focus on the most critical events by automating the Event Response process as much as possible. These platforms implement automatic movements within the framework of defined flows integrated with the security and system components of the organization or organization structure and make decisions based on the results.
Security Incident Management and Correlation System
The Event Record Collection, Analysis and Correlation System (SIEM) is at the heart of the daily operations and detection capabilities of a network facing current threats. The need for analysts of a 7x24 network to quickly display the dashboards, trends and events they need, to make threats management more effective, to identify and monitor malicious internal and external actors, and to place SIEM at the center of the next generation CSOCs. In addition, the requirements for compliance with legislation and corporate standards also require the SIEM system.
SSL VPN and SSO Applications
There has been a significant increase in the number of mobile workers who have been remotely connected to workplaces. In particular, for security reasons, some application and file resources have been made available through SSL/TLS virtual private networks (SSL/VPN). When SSL/VPN systems are widely used, they must be high-performance, expandable and easy to use. In addition, with the integration of a single-point login (SSO) method, mobile users are provided access to multiple applications without being exposed to complex input methods.
SSL/TLS Visibility Appliance
In today's internet access and almost every application of the traffic decoding methods have been used very often. Research shows that more than half of the internet traffic is encrypted. In the case of corporate networks, the situation is similar, but needs to be examined in line with the needs and security requirements. For these needs, SSL/TLS Visibility Systems offer the ability to enable high-volume encrypted traffic to be opened with Man-in-The-Middle or Out-Of-Band methods, and to send it back to security devices that will carry out the review and to re-encrypt it.
Threat Deception and HoneyPot Solution
The intrusion of intruders into the network structure, which is a danger to institutions or organizations, has become an event that is almost certainly looked at. An advanced method to prevent an attacker from infiltrating or destroying valuable data is to deceive the threat.
The main aim is to direct the attacker to the systems that he realizes and to inform the main defense systems while dealing with these systems. Deception of data, services and systems and the attacker can also provide valuable intelligence data by revealing the attacker's target and tactics.
The main aim is to direct the attacker to the systems that he realizes and to inform the main defense systems while dealing with these systems. Deception of data, services and systems and the attacker can also provide valuable intelligence data by revealing the attacker's target and tactics.
Two Factor Authentication System
User ID and verification are one of the most basic security steps. This is the case for the Cyber Security world, but there are many options for identity theft. For the solution of these problems, validating the user with different factors can provide an effective layer of security. Identity security can be ensured by these solutions, which are known to the person, or which can be used biometrically.
URL/Content Filtering
URL/Content filtering systems serve as a proxy server to enable users to access the Internet safely. Thanks to their superior inspection and detection engines, reporting interfaces and notifications, user access can be monitored instantly. Many controls and integrations can be provided against the threats that may arise over the internet:
- Antivirus control
- URL/domain filtering based on category and/or specific criteria
- Reputational control
- Application control
- SSL termination
- Bandwidth control
- APT integration
- SIEM integration
- DLP integration
Vulnerability and Compliance Management
It is a worldwide accepted fact that there are various weaknesses in every software used. Research shows that the known weaknesses are frequently used in attacks. With the regular analysis and weaknesses of the network structures, the weakness and compliance management technologies are used to ensure that the laws, regulations and regulations to be followed by the institutions and organizations working in various sectors must be followed. This information, which is derived from the compilation of the data collected from various data sources by the active and passive screening of the structure, plays an important role in increasing the security levels of the institutions.
Web Application Firewall
Web-based applications have been exposed to many attacks for many years. At the beginning of these attacks injection (such as SQL, OS, XEE and LDAP), XSS, CSRF and DoS / DDos can be sorted. Generally, security code is overlooked when the application is coded and software hackers who know it will be leaked by using these types of attacks. At this point, the Web Application Firewall (WAF) solution provides advance protection against possible attack scenarios that a software hijacker can use with thousands of signatures, custom-written policies and reputation services. It provides a precaution against the DoS / DDoS attacks with specific definitions, and against the leakage of data that meet the criteria.